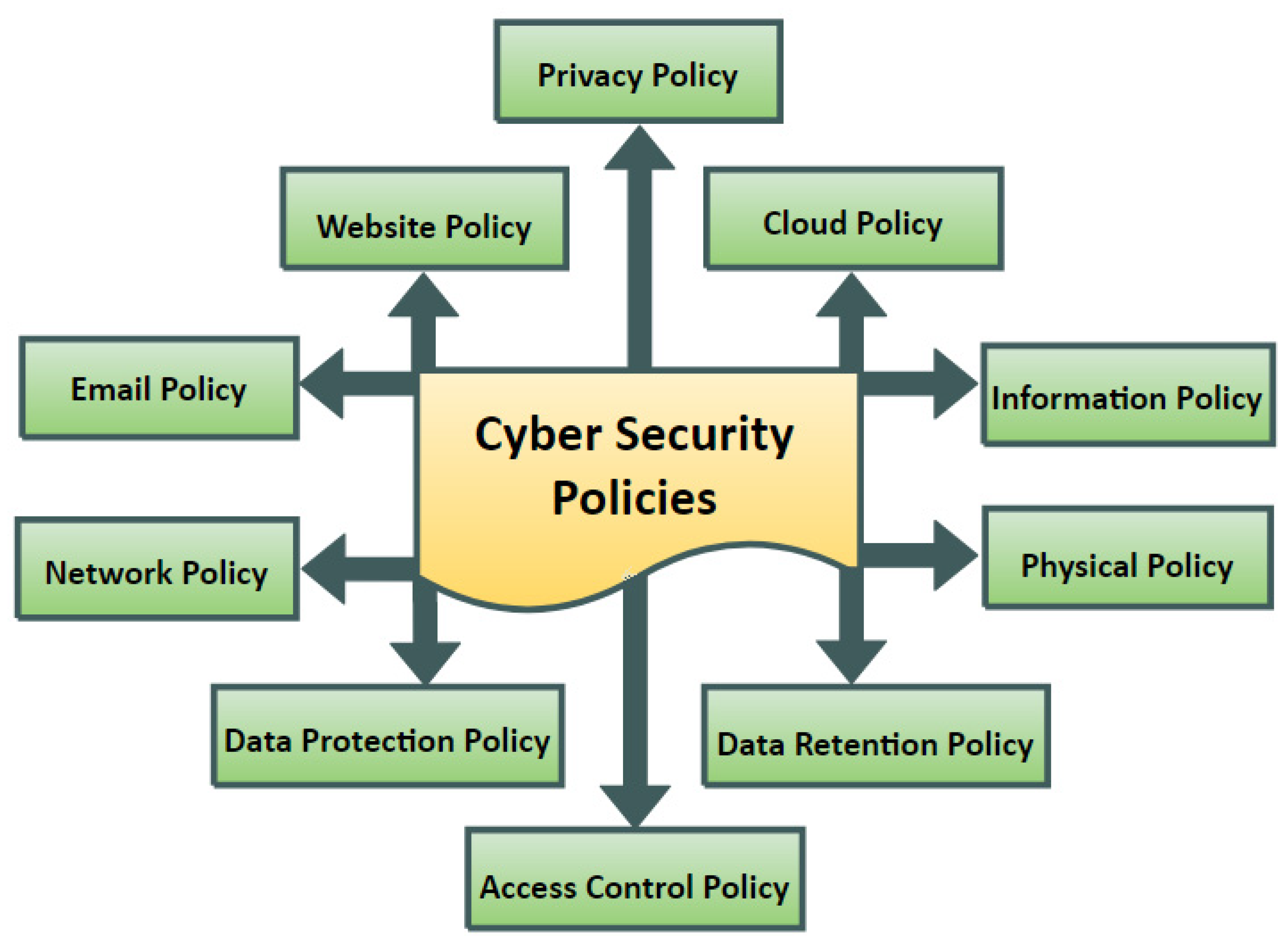
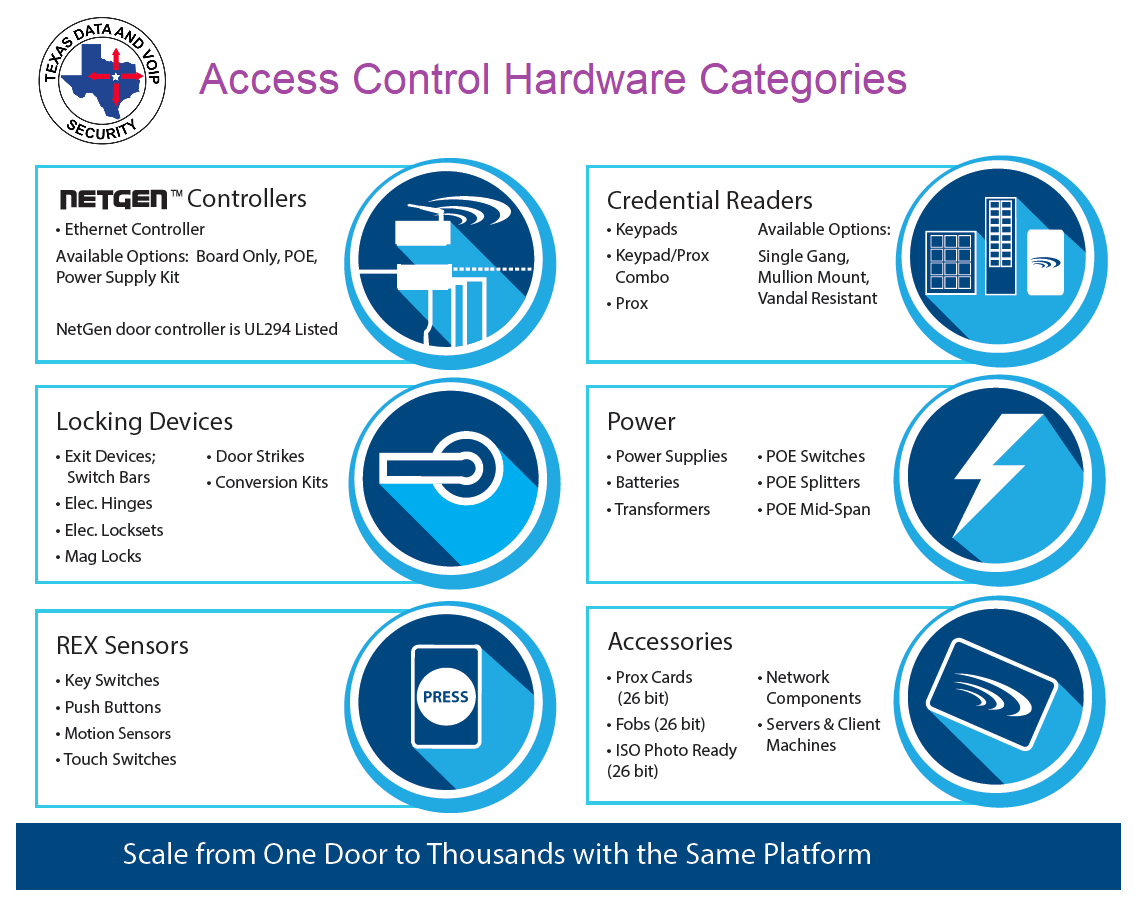
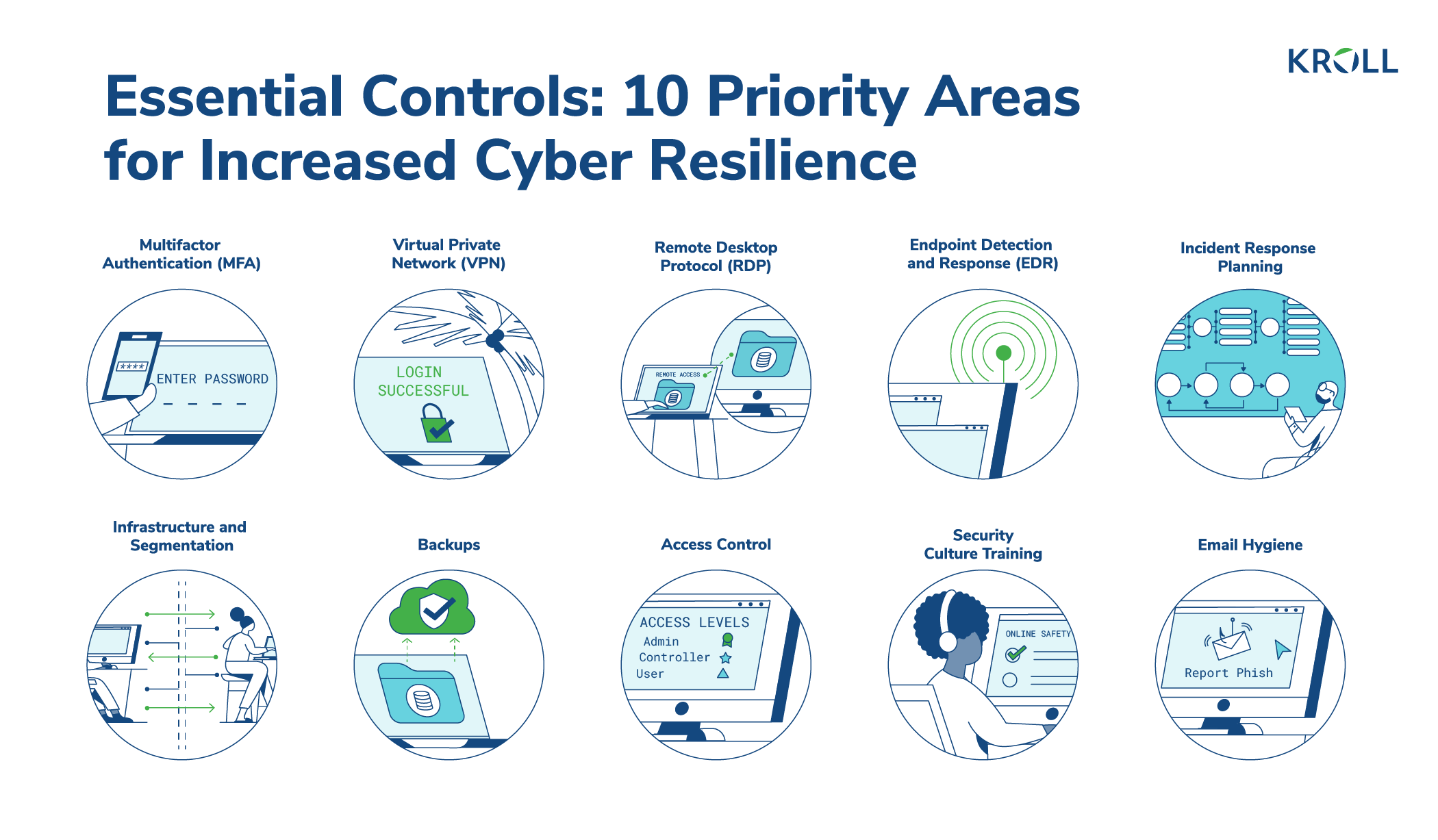
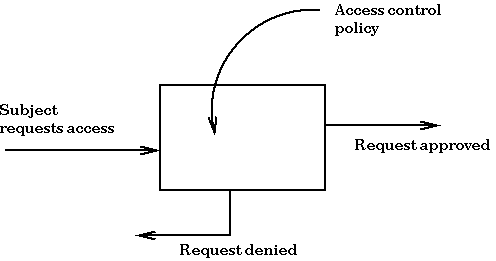
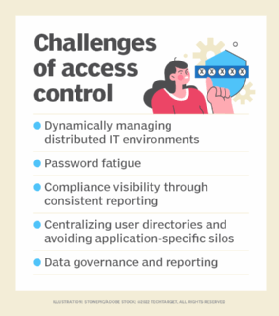
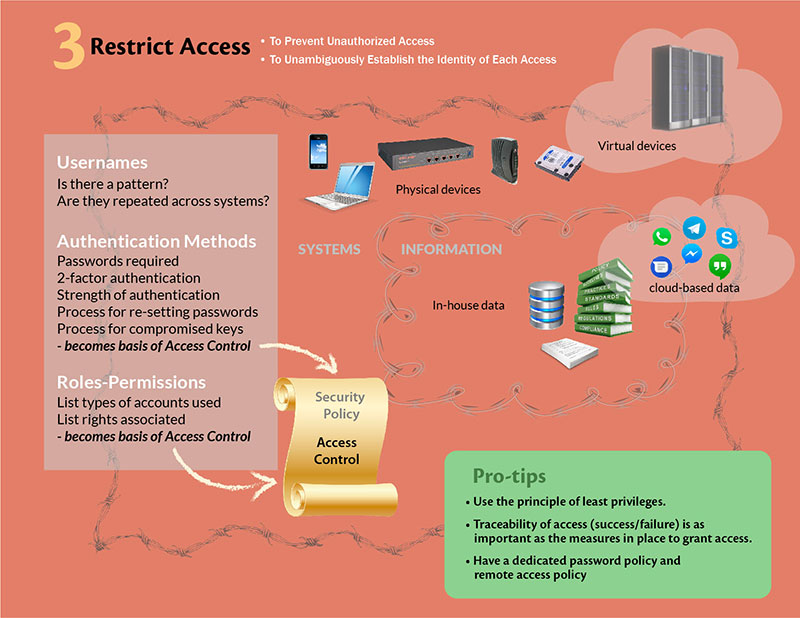
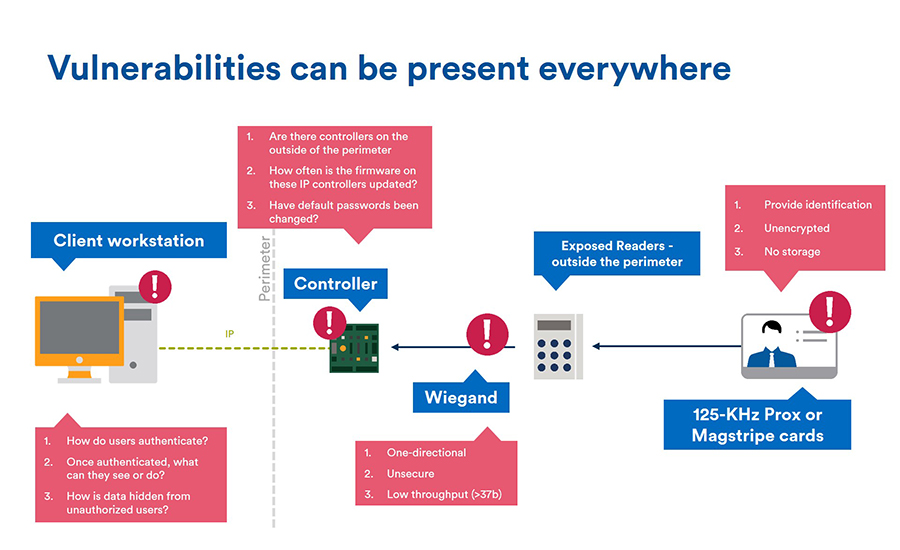
Access Control | User access control | Access Control system |Network access control | Infosec - YouTube
Information Security Define Access Control Measures For Employees Ppt Icon Pictures PDF - PowerPoint Templates
Access Control Methods Information Security Ppt Powerpoint Presentation Pictures Visual Aids Cpb | Presentation Graphics | Presentation PowerPoint Example | Slide Templates

A systematic review on security in Process-Aware Information Systems – Constitution, challenges, and future directions - ScienceDirect